The cybersecurity and entertainment worlds are abuzz with the recent megahack of Sony Corp. Yes, again. This time criminals hit Sony Pictures Entertainment, which happens to be one of the largest motion picture companies in the world. And the hack’s consequences are already disastrous: the total volume of stolen data is up to 11 TB (yes, terabytes!), which includes many corporate secrets related to unreleased movies and thousands of sensitive passwords and social security numbers of Sony Pictures employees.
Whodunit?
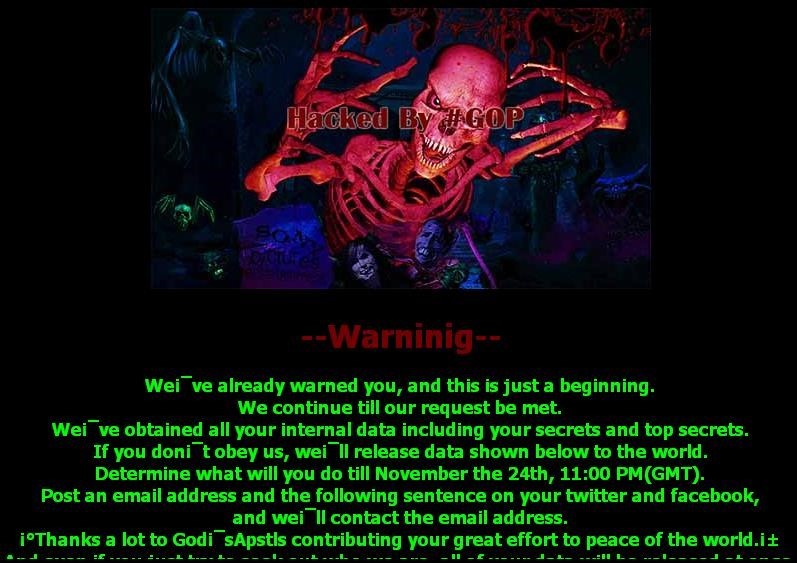
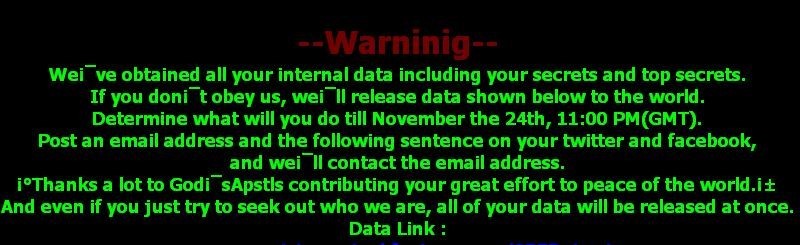
The attack apparently took place late in November, and came to light on Nov. 24th. Initial reports claimed the attackers compromised an unknown number of machines within the Sony Pictures networks, displaying this message:
This was preceded by threats sent to Sony Pictures executives:
According to Mashable, on Nov. 21 Sony Pictures CEO Michael Lynton, Chairman Amy Pascal, and other executives received a mail with the following text:
We’ve got great damage by Sony Pictures.
The compensation for it, monetary compensation we want.
Pay the damage, or Sony Pictures will be bombarded as a whole.
You know us very well. We never wait long.
You’d better behave wisely.
From God’sApstls
It’s unclear who “God’sApstls” and #GOP (aka “Guardians of Peace”) are, but they are taking responsibility for the attack. Clearly, they are not native English speakers, and it looks as though they might have used an online translation service to deliver their message.
With the doors wide open: yet another Sony megahack #enterprisesec
Tweet
There are now a lot of fingers pointed at North Korea. The claim is they were offended by an upcoming Sony Films comedy about an assassination attempt targeting Kim Jong-un. For the most part, the evidence is rather circumstantial – according to analysis of the malware used during the attack, it was constructed on a machine using Korean language packs. However, there is also evidence that would suggest the attackers aren’t well versed in Korean. Politics aside, this attack may also be financially motivated, which the aforementioned e-mail clearly shows.
How was it done?
Earlier this month, Securelist published an article by Kurt Baumgartner dedicated to the malware used in the attack on Sony Pictures’ networks. It appears to be Destover, a wiper malware capable of wiping disk drives.
The analysis shows some undeniable similarities between Destover and other malware used in the earlier attacks – DarkSeoul and Shamoon:
“Just like Shamoon, the Destover wiper drivers are commercially available EldoS RawDisk driver files.
Just like Shamoon, the Destover wiper drivers are maintained in the droppers’ resource section.
Just like Shamoon, the DarkSeoul wiper event included vague, encoded pseudo-political messages used to overwrite disk data and the master boot record (MBR).
Just like DarkSeoul, the Destover wiper executables were compiled somewhere between 48 hours prior to the attack and the actual day of attack. It is highly unlikely that the attackers spear-phished their way into large numbers of users, and highly likely that they had gained unfettered access to the entire network prior to the attack,” Baumgartner writes.
We have yet to learn how this access was gained. Some speculate the hackers could have entered the network by taking over the PC of a system administrator, who had rights to access sensitive information about Sony’s customers.
Initial attack vectors are always difficult to pinpoint, but attackers routinely use phishing emails with malicious payload – similar to what we have observed investigating the new Cloud Atlas APT.
Also of interest, the graphics used during the DarkSeoul and Destover incidents are very similar, at least in style, to the ones used in this recent Sony hack: The red skeleton is reported to be drawn by R. L. Stine.
Mr. Baumgartner also mentions that the groups claiming credit for their destructive impact – neither Whois group nor GOP – had “no history or real identity of their own”, and all attempted to disappear following their act without making any clear statements.
This time, however, there is a twist: According to The Verge, a person claiming to be one of the hackers (identified as “lena”) writes, “We Want equality. Sony doesn’t. It’s an upward battle.”
The possible hacker also wrote: “Sony doesn’t lock their doors, physically, so we worked with other staff with similar interests to get in. Im sorry I can’t say more, safety for our team is important.”
The Verge cautiously mentions that the email address possibly associated with the attacker is “an open account, which allows anyone to send mail from it without entering a password”, so it is possible that “lena” (which doesn’t look like a Korean name) had no relation to the attack itself.
There were some explicit violations of #cybersecurity ABC at SPE
Tweet
What is certain is that Sony “doesn’t lock their doors”.
With doors wide open
Soon after the attacks hackers started releasing the looted data. Within the data dump there was a file directory explicitly titled “Passwords” which included 139 Word documents, Excel spreadsheets, zip files, and PDFs. Guess, what they contained.
“Go ahead and slam your head against something hard. We’ll wait,” Gizmodo wrote. So true.
This is particularly frustrating if you recall the 2011 incident with Sony PlayStation Network. It was revealed that the passwords of PSN users were kept unencrypted, in plain text.
It’s the same story all over again. This time, include “hundreds of clearly labeled Facebook, MySpace, YouTube, and Twitter usernames and passwords for major motion picture social accounts”. The attackers didn’t have to look very hard. All this data wasn’t just sitting in plain sight, but also was clearly labeled.
Aftermath
The breach is being investigated as a purely criminal act. At the same time Sony IT departments will have to deal with the consequences of their own security shortcomings, and those border on criminal negligence.
The hack has sent giant tremors all through the entertainment industry: a lot of ugly things were exposed from behind the scenes and it’s enough for the yellow press and gossip sites to gnaw upon for weeks and, possibly, months.
The fate of the next James Bond movie, Spectre, seems less certain now, too. A lot of spoilers concerning the film have surfaced, including the fact that it’s already “massively over-budget.” Ironically, in the previous Bond film the main villain is a brilliant hacker.
Sony is, once again, in deep trouble. It faced a lot of vitriol and toxic fallout after the PSN breach in 2011, and that led to massive financial and reputational losses. This time it looks much worse, especially since the hackers exploited IT security mistakes very similar to those which led to the 2011 PSN super outage and data leak.
These mistakes are rather basic security violations: no passwords should be stored in a folder or file with a name indicating what they are; no passwords should be kept unencrypted, in plain text, and the same is true for the other sensitive data. The passwords themselves are reported to be very weak, which is another IT management mishap. This is going to cost the corporation and its workers whose personal data are now exposed.
For more information on data encryption, refer to this article.
And by the way: A new version of Destover has just emerged, already signed by a legitimate certificate stolen from Sony. It didn’t take long.
 Destover
Destover


 Tips
Tips