According to the results of the “Mobile cyber-threats” survey carried out by Kaspersky Lab and INTERPOL between August 2013 and July 2014, every fifth Android-based device protected by Kaspersky Lab security solutions was attacked by malware at least once during the reporting period. In 60% of the registered attacks the malware used had a “financial” nature – i.e. its purpose was to steal users’ money.
The ups and downs of mobile threats #security
Tweet
Well, this would be just yet another unexciting cyberwar example, reiterating something quite well-known already – the “utter unsafety” of Android as the most targeted mobile operating system.
There are, however, several twists in this case.
According to the survey, a total of 1,000,000 Android device users around the world encountered dangerous software between August 2013 and July 2014. This represents about one fifth of all Kaspersky Lab mobile product users. More than 588,000 Android users worldwide faced financial malware (Trojan-SMS and Trojan-Banker, with Trojan-SMS accounting for 57% of attacks) during the reporting period – i.e. almost 60% of those users.
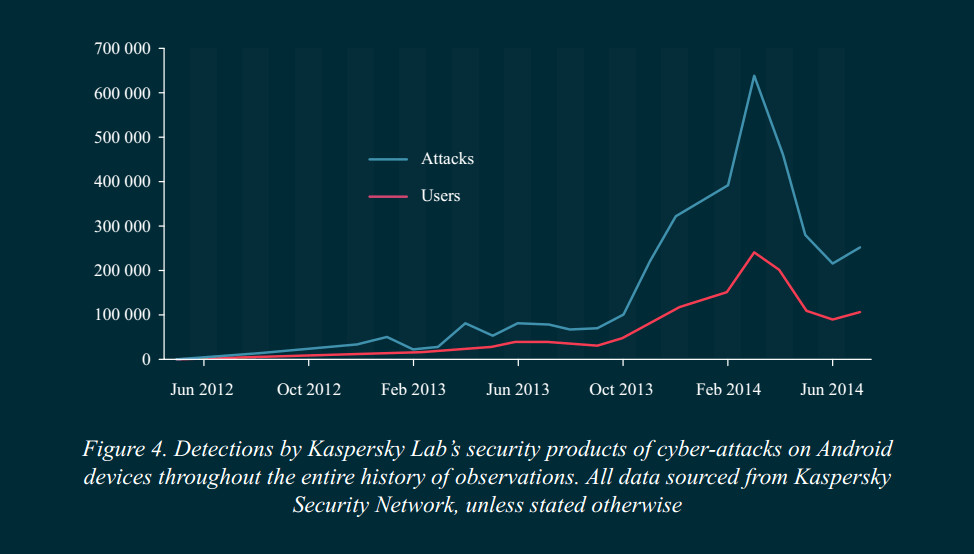
Therefore, today’s malware writers are mostly engaged in earning money. But let’s look at the graph below:
The huge spike, then the sharp drop. The spike detected between February and April, 2014 is mostly attributed to an influx of Trojan-SMS family. These accounted for 57.08% of all detections made by Kaspersky Lab security solutions for Android-based devices. Aside from the number of attacks, the “diversity of species” among this sort of malware sky-rocketed as well: our experts found the number of mobile malware modifications grew sharply – from 423 in August 2013 to 5,967 in July 2014, a 14-fold increase.
Modifications aren’t exactly new malware, they’re just altered versions of the existent malicious programs. “A Trojan-SMS needs to infect dozens or even hundreds of devices to show a worthwhile profit”, said Roman Unuchek, senior virus analyst at Kaspersky Lab. So malware writers create modifications of their programs, creating “slightly” different variants, expecting to spread them out as far and wide as possible. Hence the reason why Trojan-SMS malware is encountered more often.
The abundance of the Trojan-SMS malware in the global statistics is also the reason for the sharp drop in the numbers of attacks detected after April 2014.
Malware authors feed on loopholes and flaws. #security
Tweet
Actually, Trojan-SMS malware has mostly been (over 50% of cases) attacking Android users in Russia, that until quite recently was a very lucrative medium for them. Then “all of sudden” the rules of the game changed: new regulations required all Russian operators to send a confirmation message from any subscriber who is trying to pay for services via SMS. This effectively meant that sending out the SMS to paid numbers without a user’s knowledge and consent wasn’t as easy as before. And thus seeding around the older-type Trojan-SMS malware became much less lucrative than before.
However, in July the number of attacks started climbing again: criminals were apparently trying to fight back. The drop mentioned above shows that removing the “nutritive medium” – by whatever means – can be very effective. In this case, the “legislation patch” requiring a confirmation message from a subscriber every time, helped to remove – even if temporarily – the “harvesting” of money using the most common mobile Trojans.
Malware authors feed on the weaknesses, loopholes and flaws of the systems they do their “business” in – for as long as they have a way to do it. Once it is no longer available, the party stops – at least, until they find yet another loophole.
And if we speak of threats that vulnerable personal smart devices and mobile malware may pose for corporate networks in companies with BYOD adopted, the risks are decreased dramatically if the most apparent loopholes are plugged – a centralized antimalware solution is installed on all of the employees’ devices, MDM tools are in place and working, the company’s electronic payments are protected. This would diminish the possibility for attack, based on the most “common” mobile threats.
The full version of the joint survey of mobile threats by Kaspersky Lab and Interpol is available here.
 android
android

 Tips
Tips