What’s it like to work with spam? No, not spamming out everything you’ve got, but vice versa. What’s it like to find ways of not letting spam through?
Academically, it must be quite an exciting study, possibly not unlike entomology (although actual spam analysts may disagree with such a comparison). Why would businesses care about the spam and its trends? On the surface, it’s about knowing the spammers’ tricks, those who do their best to attract undeserved attention to the advertised offers. On the darker side, spam is also used to spread malware and phishing letters. So, knowing spam is knowing thine enemy. Sort of.
We have a Q3 spam report by Kaspersky Lab. So let’s take a look.
Spam and Phishing in Q3: Dirty Summer Tricks #spam #q3
Tweet
Summer moved on
The first highlight is that spam levels have moved upwards. Very slightly, though, just 0.8% up from the average percentage of the previous quarter (currently it’s 54.2% in the overall email traffic). It was predictable, as vacation season effectively ends in Q3, and spammers tend to leverage this.
This was actually observed: Exploiting the summer holiday season, fake notifications from booking services, airlines, and hotels were used to spread malicious programs such as Trojan-Downloader.JS.Agent.hhy, disguised as a flight e-ticket or hotel reservation.
Another type of spam email offered a selection of brides (mainly from Russia and Ukraine) to foreign suitors. After replying, targets were sent further spam emails as some “brides” asked for money to visit their “suitors”.
There was also “the sheer variety” of dating-themed spam in Q3 – all kinds of dating/marriage/adult sites were spamvertised, as well as a (sort of) new type of spam, blatantly fraudulent. A mass mailing was observed that prompted recipients to send a text message to a specific telephone number – in return a girl promised to send intimate photos of herself. A little bit of checking showed that this was a robot doling out a mobile malware on the other end.
Dating fraud and new tricks with PDF full of malice: #spam in Q3
Tweet
Newer tricks
In Q3, cybercriminals came up with a new way of distributing phishing emails and bypassing spam filters. The text of the phishing email and the fake link were included in a PDF document attached to the email. After clicking the link, a standard phishing web site opened and the user was asked to enter his personal information.
The majority of emails utilizing the new technique imitated bank notifications. The body of these messages usually contained a short text describing the problem; sometimes there was no text at all.
The spammers used well-known phrases and tricks in the text of the emails: notifications about an account being blocked, the need to pass a verification procedure, security issues, an investigation into phishing incidents, etc. As usual, the fraudulent links were masked by legitimate links and text fragments.
https://media.kasperskydaily.com/wp-content/uploads/sites/92/2017/05/06020412/q3_2015_spam_eng_9-1024×532.png
Another trick was sending spam imitating a non-delivery auto-reply sent by an email server, which contained a malicious ZIP archive with Trojan-Downloader.JS.Agent.hhi. This in turn downloaded Backdoor.Win32.Androm.
Rise of the Phishers
Phishing activity keeps going up: according to Kaspersky Lab stats, in Q3 2015, the Anti-Phishing system was triggered 36,300,537 times on computers of Kaspersky Lab users, which is 6 million times more than the previous quarter.
‘Global internet portals’ (30.93%) topped the rating of organizations attacked by phishers although its share decreased by 11.42 p.p. from the previous quarter. Yahoo, Vkontakte, and Facebook appear to be the most targeted.
The share of ‘Social networking sites’ (21.44%) increased by 6.69 p.p. In third place came ‘Banks’ with 18.07% (+4.65 p.p.). The ‘Online games’ category also increased by half and accounted for 4.02%. Games draw an increasing interest from the criminals, as there are a lot of end-users’ money involved.
Full text of the latest Q3 report on spam and phishing is available here.
 phishing
phishing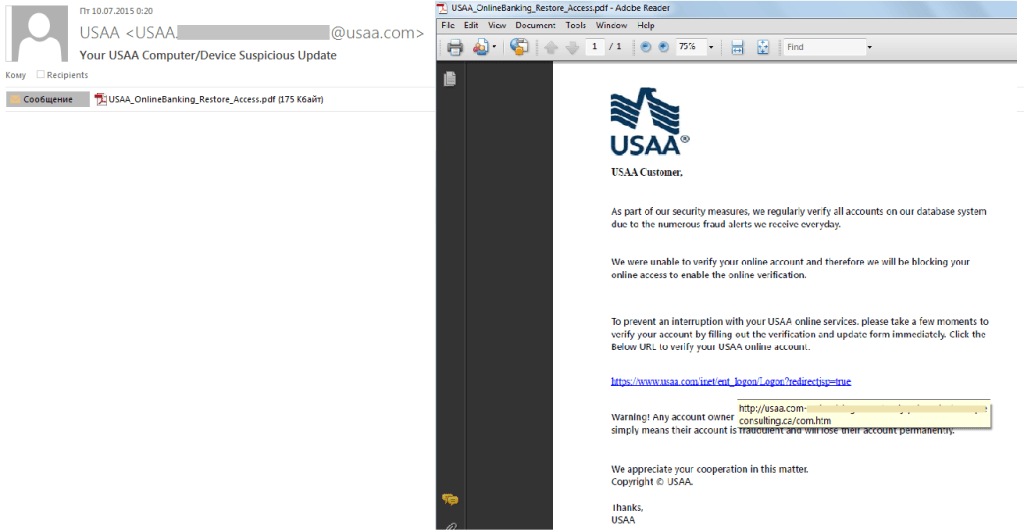

 Tips
Tips