Incident response is a major long-term cybersecurity challenge that must be addressed by businesses to ensure their stable development. For the IT security industry, incident response will soon be where the most advanced technologies come together. Aside from leveraging revolutionary technology, incident response requires major day-to-day efforts to obtain, store and analyze a large trove of relevant security intelligence. In order to be successful, this process has to be tightly integrated with existing IT security solutions and should be powered by the threat detection solutions of the future.
Things we have learnt from the detection challenge
Three years ago when we started working on our specialized solution to discover complex threats and targeted attacks, we already knew that there never be a “silver bullet” to address this problem. Each targeted attack is unique: threat actors are fine-tuning their tools and techniques for every new victim, depending on the goals perceived and specifics of the infrastructure. Targeted attacks involve complex multi-stage processes that include initial infection, lateral movement and data exfiltration. At many of these stages, or even all of them, the use of malicious code is not even required by the attacker. A detection solution therefore has to deal with this, and be able to spot an attack at any stage of its development.
This is very different from well-established approaches to threat prevention. Although there are still many challenges for the efficient blocking of widespread malware, in general this is a problem solved. In the case of a targeted attack or a new, previously unknown, sophisticated malicious code (which may belong to the attack vector), the only effective solution is to constantly search for anomalies in the corporate workflow. It is worth noting that the following approach is relevant only when all known, detectable, clearly malicious actions have been filtered and blocked. This is up to 85-90% of everything being thrown at a company from the outside.
Rules of detecting the unknown
- Initial infection: the solution has to be more paranoid than your typical endpoint security suite. True Cybersecurity has the power to operate in many shades of gray, it’s not only ‘malicious’ or ‘benign’. Suspicious objects have to be further analyzed. Their behavior and intent has to be tested in an isolated environment. They should be checked against known and constantly updated threat actor tactics and techniques. Even if an object is not deemed malicious outright, it should be detected eventually: it is better to detect an attack later than never. And all key nodes should be covered: including network traffic, endpoints, and e-mail.
- Lateral movement and exfiltration: the solution should be able to discern typical network traffic and endpoint behavior from an attacker’s behavior. This requires a definition of the ‘normal operations’, unique for each company, as well as knowledge of the various ways threat actors investigate their victims and obtain what they want.
In a nutshell, targeted attack detection is real-time threat intelligence, plus continuous data processing, plus intelligent machine learning algorithms. Last year we realized these requirements in our Kaspersky Anti Targeted Attack Platform, and offered security officers of large businesses a chance to automate a very complex problem solving scenario. We blended intelligence, data processing and machine learning to partially replace a highly skilled security expert – a rare, sought after and highly expensive professional. But what’s next?
From detection to response: more data plus millions of indicators
Targeted attack detection is a major step towards remediation, but only the first one. Response and remediation brings additional challenges and requires more data. What endpoints were affected? Which users? What happened on the network? Is there a chance that an attacker is hiding inside the perimeter? The amount of data required for an efficient response is many times greater than the amount of data that makes detection possible. Response needs more data: as granular as the smallest changes in the Windows registry, files dropped, network requests and many more. Building a system to collect such vast amounts of data, and store it in a meaningful form, is already an immense undertaking. But there is still more to do.
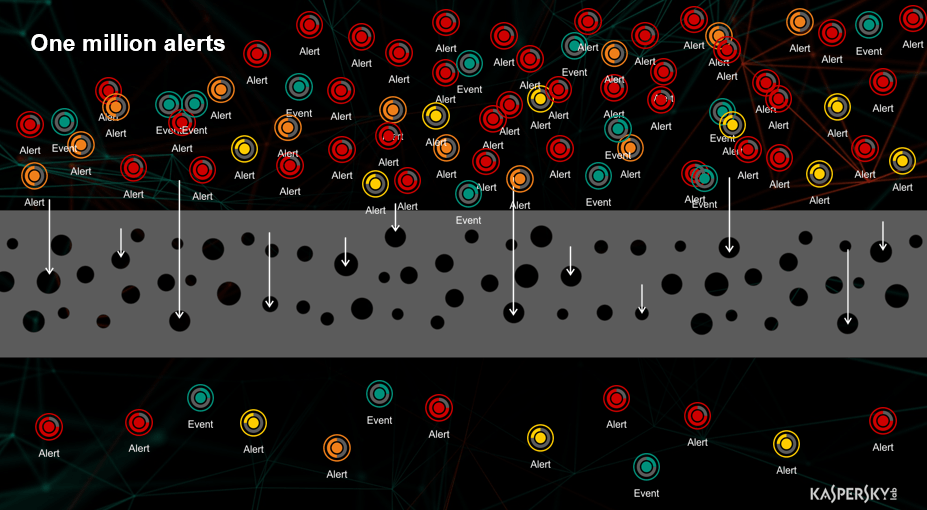
Basically, as we build a data acquisition framework to support incident response, we expand the approach already embraced by many enterprises. To ensure better visibility of what’s happening in the network, these businesses are storing and processing many events in a SIEM system. Even at the detection stage this brings them a major problem: millions of alerts. The ideal scenario where nothing happens until a major threat is detected and grabs the attention of SOC staff is impossible to achieve. In reality, a major threat is dispersed among millions of alerts, and thousands of security incidents of different kinds, each taking away precious resources. This is detection. Take response into account and you can easily multiply the avalanche by a magnitude. Before this mess reaches the eyes of a security officer, it has to be filtered and organized.
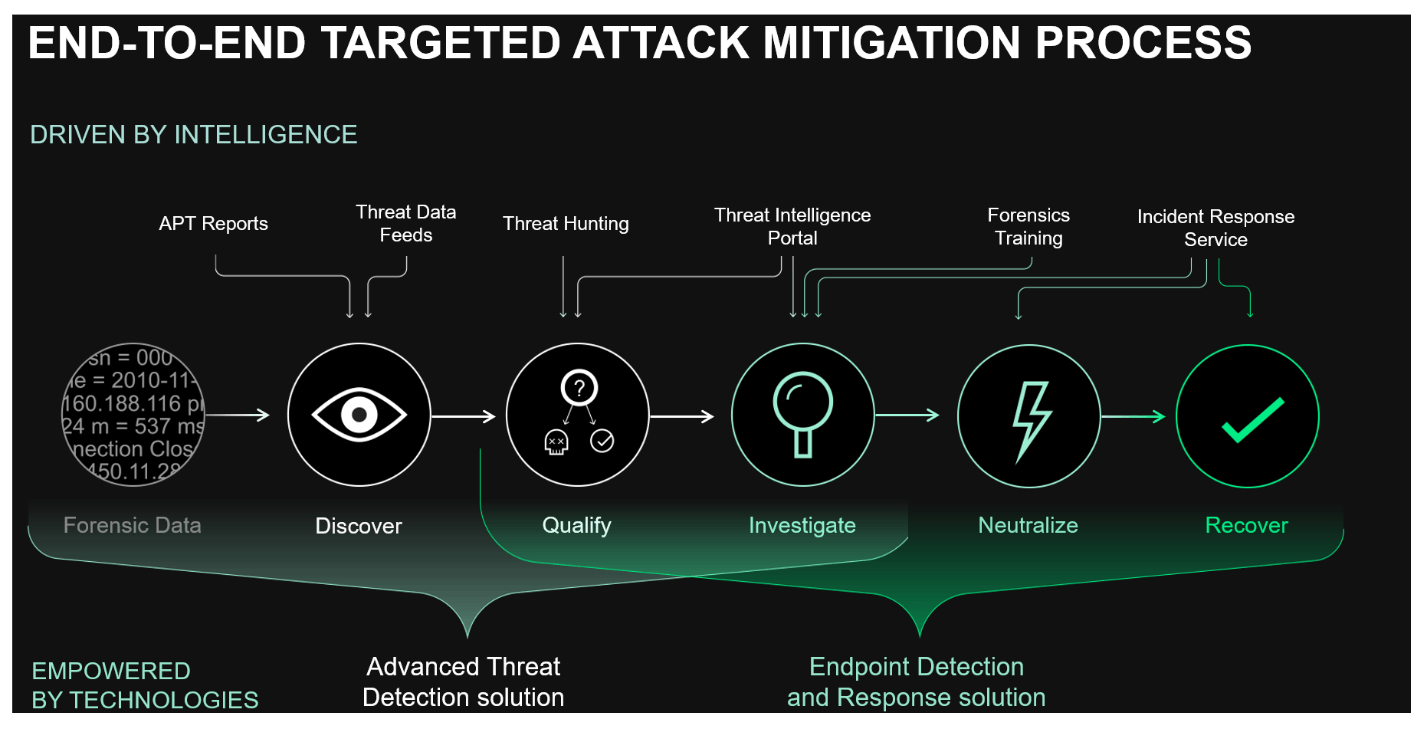
This brings us to a major conclusion. Although the need for better security intelligence and better visibility is undisputed, approaches to produce actionable threat response are different. Obviously, endpoints are a top priority for response technology, as they store the widest range of crucial information about an incident. Controlling endpoints so that any data can be taken for incident forensics at any time is also a must.
But the only way to spare corporate SOCs from millions of alerts is to develop detection and response technologies in an integrated form. In our view, detection and response will only be efficient if they are based on a single data acquisition and processing entity that is able to combine various clues from various parts of the infrastructure in one place. As we are work to further develop our detection and response offer for enterprises, we are going to stick to this approach. Our Next Gen highly adaptable enterprise security system will have many sensors, operate with thousands of different object types, and apply millions of rules based on our threat intelligence. But it needs to have only one brain.
 HuMachine
HuMachine

 Tips
Tips