Believe it or not, math is important. While it may have been easy to roll our eyes at our childhood schoolteachers, human behavior is quite predictable and math helps in those predictions: at least us, humans, can be described with math when it comes to our behavior. The good news is that also applies to cybercriminals.
Hackers and other criminals, who use Internet for “work” (like drug and gun dealers) put a great deal of effort into staying anonymous: they use Tor to get online, change their handles (nicknames used at underground forums) and use special anonymizing tools.
With that said, cybercriminals are still human and are heavily limited by their social habits and surrounding. They celebrate New Year, sleep at night and go to work. Besides, they are also unable to post from several accounts simultaneously. In theory one can make a bot, which publishes something at the same time the hacker does, but that’s quite another story.
RT @chthierry: How #BigData helps to catch criminals: https://t.co/nIu1L9sd4S via @kaspersky
— Kaspersky Lab (@kaspersky) January 5, 2016
All of the online activity creates data and when you have enough data for analysis, it makes it a bit easier to catch a criminal. There a lot of analytical companies that do forensic research for law enforcement agencies. One such company is Recorded Future. At the Security Analyst Summit 2016 the company’s CEO Christopher Ahlberg revealed how they use math to catch criminals online.
The company automated data collection processes to gather information from more than five hundred forums, which are popular among cybercriminals. Data has been collected in seven languages for more than four years. As a result, Recorded Future discovered several interesting facts.
Non-Impervious: #cybercriminals make mistakes too: https://t.co/WC8392Uwh3
— Kaspersky Lab (@kaspersky) February 27, 2015
Interestingly enough it appears that cybercriminals rarely reuse handles. Recorded Future tracked 742,000 nicknames — and 98.8% were unique. Despite that, analytics can detect, which nicknames are used by one and the same criminal. Handle hopping is easy to change, but changing behaviour is much harder.
Awesome talk by @cahlberg proves even hackers can't escape pure math and psychology, you are traceable #TheSAS2016
— Christine Gadsby ღ (@ChristineGadsby) February 8, 2016
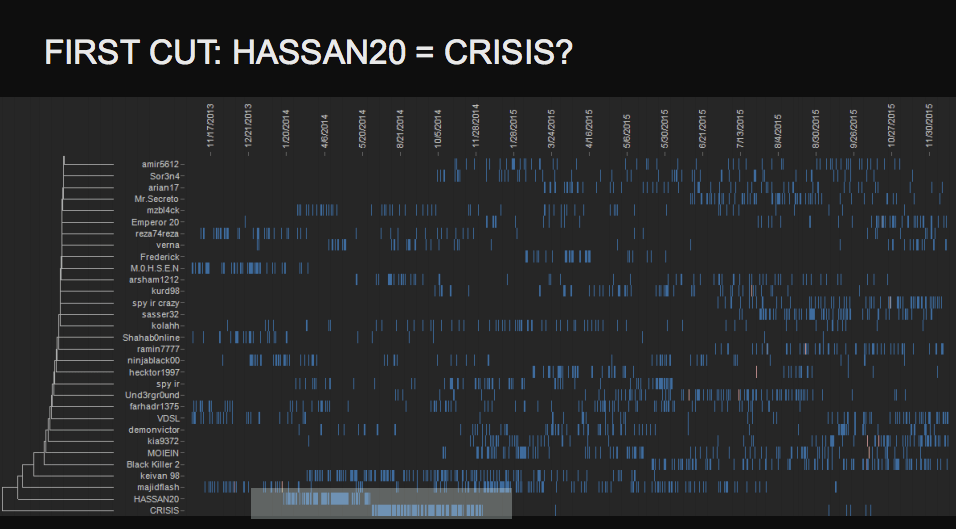
Having analyzed activity schedules and speech patterns, one can find connections between different accounts looking absolutely unrelated. The most obvious thing that attracts attention — it’s the timetable of Internet activities. If different accounts go online one after another, like train cars, it’s quite possible that they belong to the same person.
As you can see on the screenshot above, as soon as Hassan20 user goes offline, Crisis user logs in. Maybe, these accounts belong to one and the same guy. One can use this method to single out members of one band: for a decent period of time they will be active simultaneously to coordinate their business.
If members of one group remain online all day round, they either live all over the world in different time zones, or try to create such an impression.
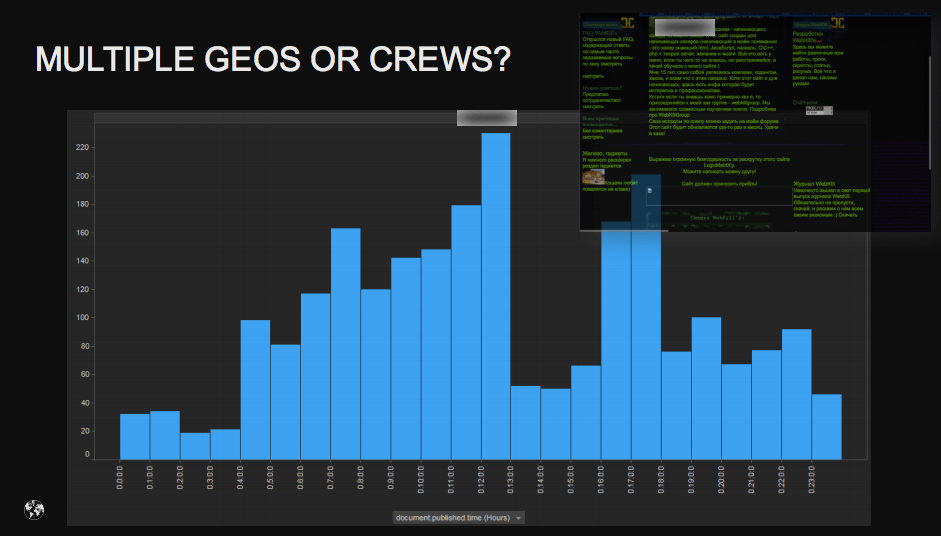
Having studied hackers’ days off and periods with the greatest task load, one can single out their nationality. For example, there are high chances that criminals from Islamic countries will be active during Ramadan. Well, if you are not religious — there’s not much to do but to ‘work’ during these days? Besides, they are also quite active during the celebration of the anniversary of Islamic Revolution. As for Russian hackers, they work the hardest during the last week of December. What’s interesting, New Year is celebrated by everybody, even cybercriminals.
One can single out other, more specific signs and traits and find users with similar habits not on the dark net, but on the legal Internet. Criminals have hobbies, just as we do. They use social networks, go on vacations, use different web services to watch movies and read books. As opposed to Tor, these services give you more chances to find out their real identity, and in the end, arrest them.
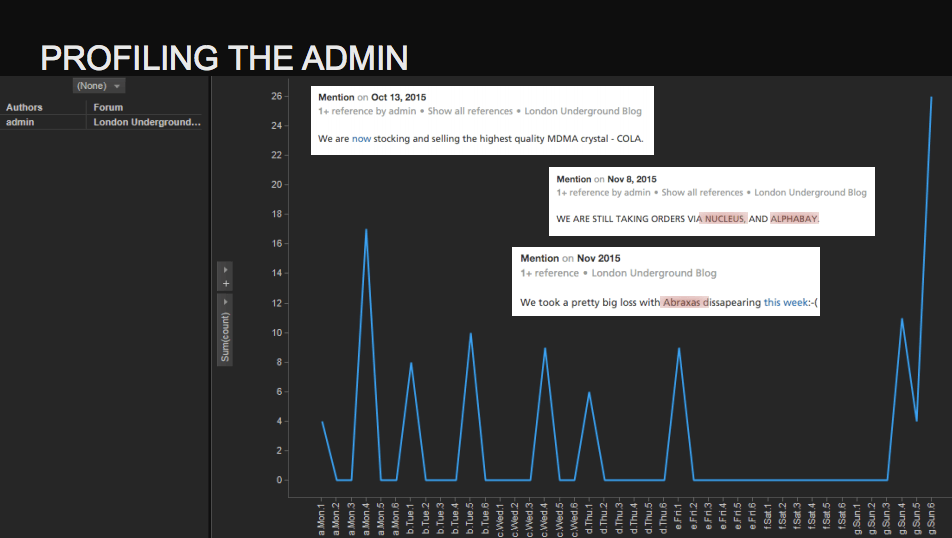
Having analyzed activity schemes on a London underground site, which sells drugs, you can see, that user Abraxas is the admin of the resource. Ok, what do we have on him? It looks like he was away for two days, which resulted in a money loss for the drug dealers. Did he go on a vacation? Or maybe caught a cold? When forensics agencies have enough of these facts, they’ll be able to find a real person.
Moreover, there’s no need to limit yourself with passive observance. In some cases it’s much better to make them change their behaviour patterns with a provocation so that they would betray their instincts. Christopher claims that he knows of several investigations, which turned to such trick and it worked quite good, but he cannot reveal details for the safety sake. So we will analyze this method with the help of a well-known example.
Cybersecurity experts are aware of the following principle: once a developer produces a patch, somebody promptly reverse-engineers it and creates an exploit. As many people do not install system updates in time, they will become the targets of a zealous cybercriminal. As Microsoft had a habit to release patches on Tuesdays, a saying: “Patch Tuesday, exploit Wednesday” appeared. It illustrated the above-mentioned principle.
Patch Tuesday created exploit Wednesday @cahlberg at #TheSAS2016 pic.twitter.com/RevqYIPagT
— Eugene Kaspersky (@e_kaspersky) February 8, 2016
So patches have become a double-edged weapon. On one hand, they protect people; on the other they literally give hackers a tool to hook careless users. Besides, patches on Tuesday have made hackers work hard during next days after their release.
So Microsoft has accidentally rescheduled hackers plans for each second and fourth Wednesday of the month. Security specialists can do the same and provoke hackers to reveal themselves with the help of a thought out campaign. And that’s what they do.
 analytics
analytics


 Tips
Tips