Kaspersky Lab has released its report on cybersecurity in Q3, 2014. Highlights are: the Shellshock vulnerability, Crouching Yeti/Energetic Bear, Epic Turla APT campaigns, a significant increase in the number of malicious attacks (of various kinds), and a burst of mobile banking Trojans. The full version is available here.
Shellshock, a.k.a. Bash Bug, loomed menacingly over the entire Q3. The scope of the event is actually so large that 2014 will probably remain in cybersecurity history as the year of Two Big Bugs: Heartbleed, discovered earlier this year, and Shellshock. Everything else seems pallid in comparison, but by no means should they be disregarded. Unfortunately, no one can promise that something comparable to Heartbleed and Shellshock isn’t going to occur before the end of the year.
IT #Threat Evolution Q3 2014: arms race goes on, who wins?
Tweet
Overall, there was a strong increase in number of attacks from Q2 to Q3 – the amounts are varied, depending on the nature of the problem. There was a 33.1% increase in the number of malicious attacks blocked on the computers and mobile devices of Kaspersky Lab users; 31% more unique URLs that triggered web antivirus detections, a 14.4% increase in the number of mobile malware samples added to Kaspersky Lab’s collection; there was 3.4 increase in the number of mobile banking Trojans, and the number of countries they have been detected in has grown twofold.
How should we interpret this data? Does it mean the onslaught of cybercrime and futility of all attempts to stop it? Apparently not.
An increased number of attacks means the attacks were detected and thwarted. We should focus on the attacks’ increasing futility. An increase in banking Trojans and the number of countries they infected means they are getting intercepted by security solutions, which decreases the threat they pose.
Of course, both sides are perpetually improving their trade: cybercriminals write new malware and exploits, security vendors find a way to counter them, sometimes going to such great lengths that they launch large-scale operations to dismantle infrastructures behind botnets and (banking) Trojans. As with any arms race, new weaponry is constantly added.
The number of threats, however, won’t decrease – largely due to the fact that cybercrime is just too lucrative. There are potentially great profits to be had with moderate effort. And there is very little difference between “hi-tech” and “common” crimes.
Q3 2014: A Big Bug, large APT campaigns discovered, banking Trojan keep increasing #security
Tweet
Hi-tech crime efforts don’t have to be great as long as there are large numbers of exploitable vulnerabilities in the software. More importantly, the number of people who don’t care much about their devices’ security is quite large. According to a recent survey, 1 of 8 people just don’t believe cyberthreats are real. That makes them extremely vulnerable to the attacks, but not just them: cyber-incidents usually have some “area of effect,” affecting more than just a single target. Cybersecurity is everyone’s business.
The full text of the Kaspersky Lab’s IT Threat Evolution Q3 report is available here.
 Cybersecurity
Cybersecurity
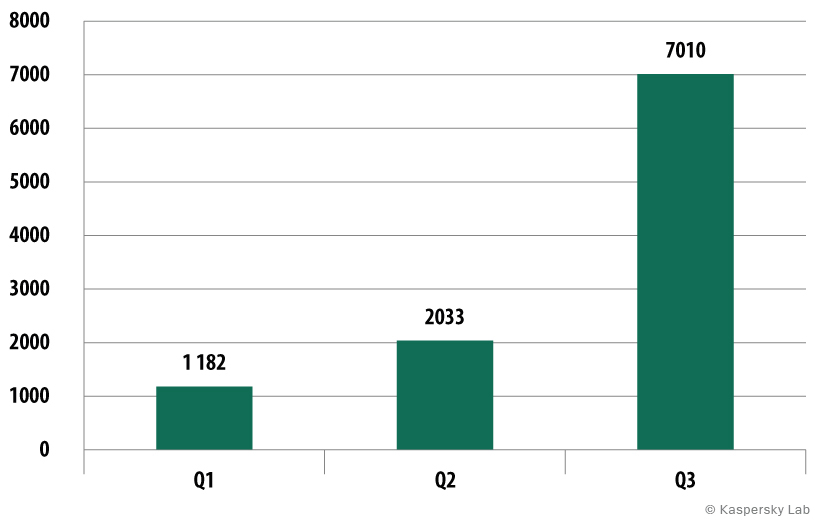

 Tips
Tips