We have written about the dangers that public Wi-Fi hotspots pose to users time and time again, but today we are talking about threats that come specifically from home wireless networks. Many wireless router users do not consider them to be threatening, but we are here to shed some light on this unfortunate reality. This guide is by no means complete, but several of these great tips can help you improve your home network security.
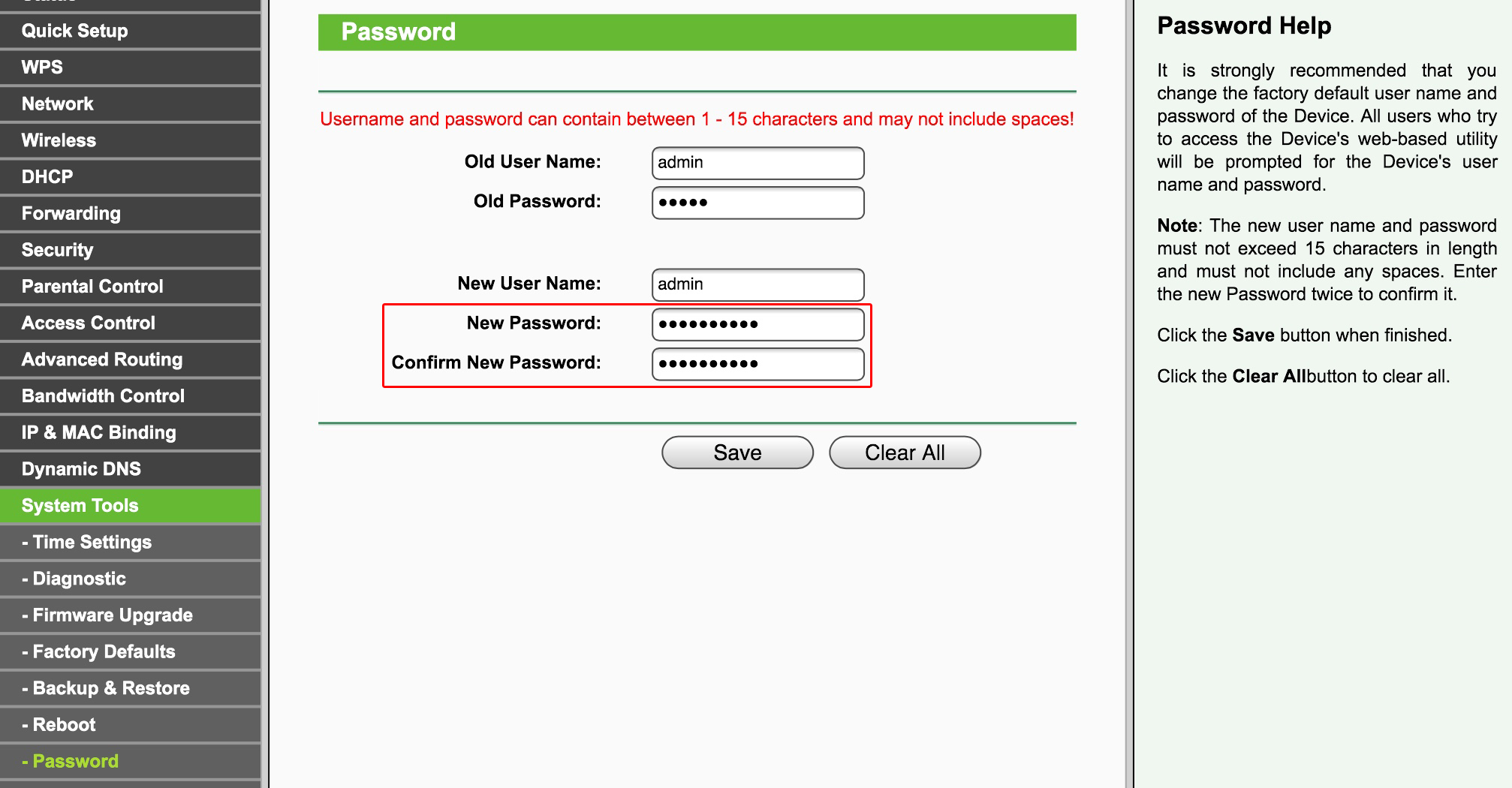
Step 1. Changing the admin password
One of the most serious mistakes often made is using the default, out-of-box, admin password (consider the frequently used “admin:admin” and “1234”). Combined with some non-critical remote vulnerability or an open wireless connection, this might give criminals full control over the router. If you have not already done so, we strongly recommend resetting the password to something more sophisticated.
To illustrate our point, we present a number of screenshots of TP-Link’s router settings. Of course, these images might look different for other vendors, but the overall logic is similar.
Step 2. Disabling remote management
A second problem that is often encountered is open access to the router’s control interface. Usually producers enable only LAN-based router controls by default, but this is not always the case. Make sure that you check whether your router’s control interface is available over the Web.
In most cases, in order to disable remote management, you should uncheck the appropriate box (in our case – enter the 0.0.0.0 address). It also makes sense to block access to the router through Telnet or SSH protocols (provided your connection supports them). Proficient users may also apply restrictions to control capabilities over LAN-based networks on the hardware’s Mac addresses.
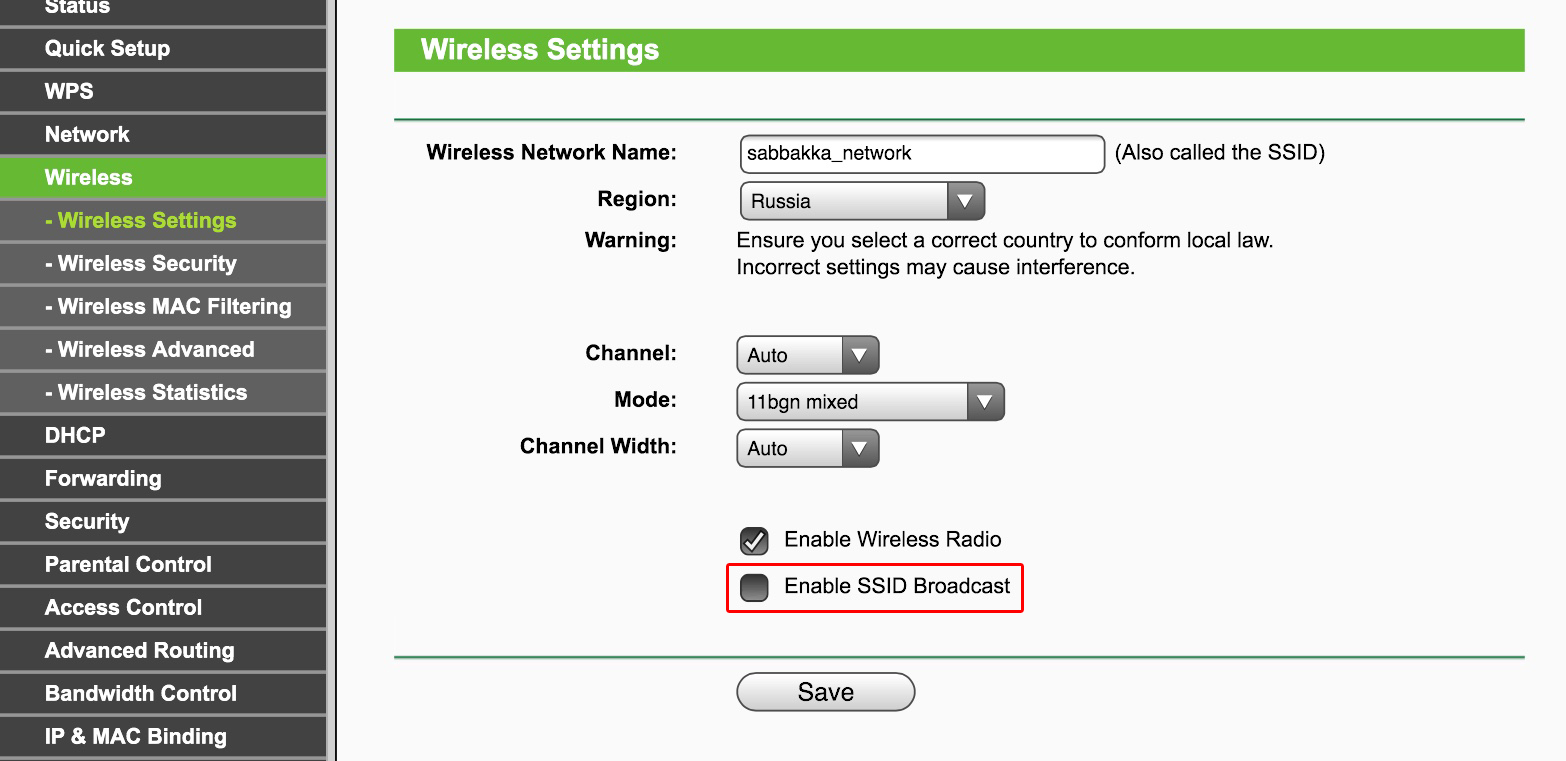
Step 3. Disabling Broadcast SSID
As a rule, a wireless router transmits your Wi-Fi network ID (the so-called SSID) to everyone. This may be changed at will by unchecking the corresponding box in the settings. Then your network will not be so easily hacked. However, as a compromise, you will have to enter the SSID every time that you connect a device to the network. This step is not mandatory.
Step 4. Using reliable encryption
Must you admit every single person to your wireless network if your subscription is unlimited? We strongly recommend that you do not. Among the usual folks, there may well be a skilled teenage hacker in search of a free connection, and you, basically, just set yourself up to be susceptible to threats that are common for public hotspots: personal and credit card data theft, loss of email and social networks login credentials, an infection of all home machines, etc.
Additionally, cybercriminals might use your home network for illicit activities and the police could end up on your doorstep! So we suggest enabling WPA2 encryption (WEP is not very reliable) and setting a stronger password for your Wi-Fi hotspot.
Step 5. UPnP et al.
Today’s wireless routers are not only capable of serving a Wi-Fi access hotspot and facilitating Internet access to LAN nodes, but they also support different protocols to automatically align and join connected smart devices.
Universal Plug and Play (UPnP), DLNA support (Digital Living Network Alliance) and the like, are better off disabled if not in use; you run a lower risk of being affected by vulnerabilities in software using these features. Here is a universal rule: disable everything that you don’t need. Should you need the feature after all — just enable it, it’s not rocket science.
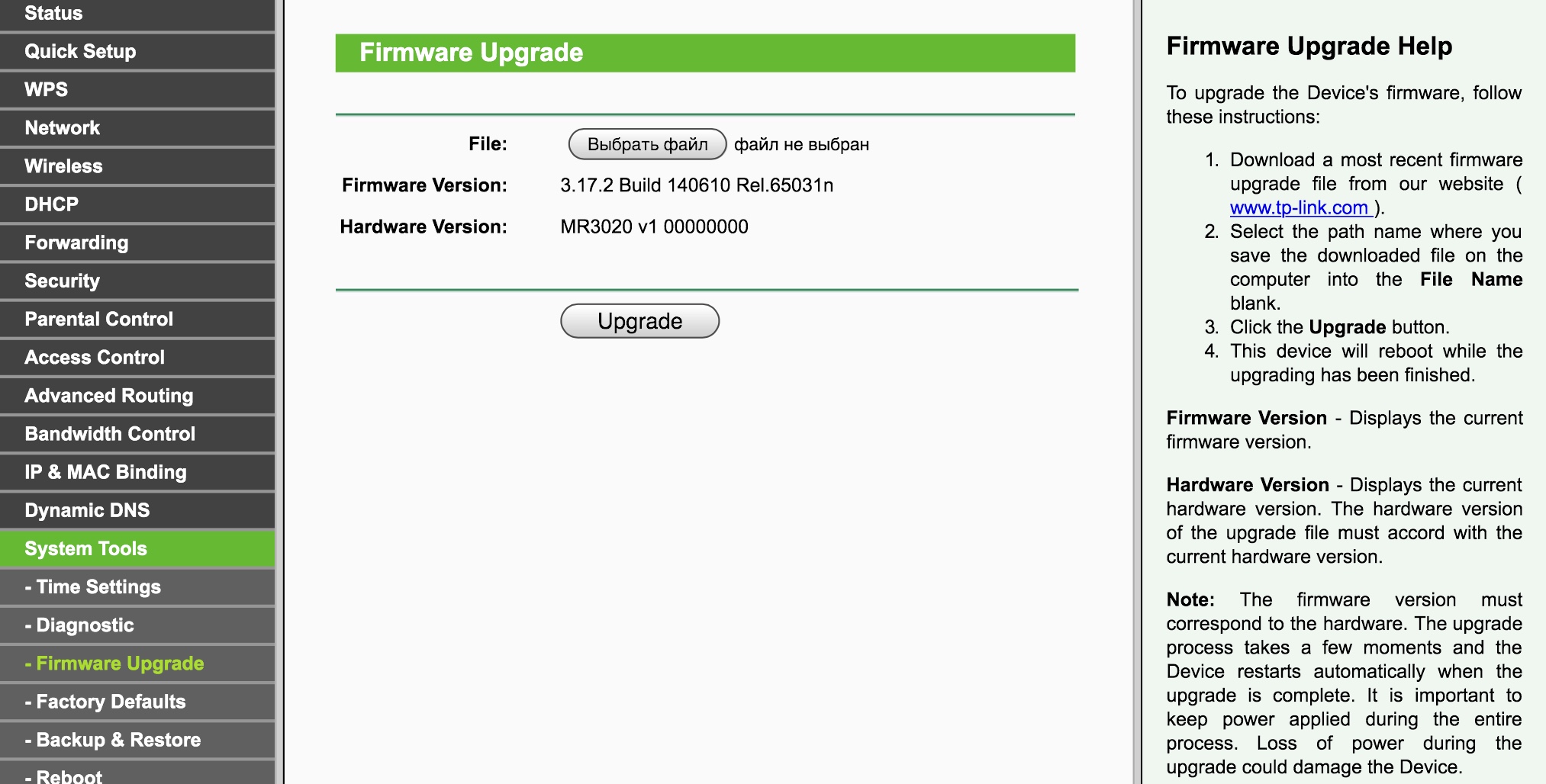
Step 6. Updating built-in software
Router owners are not good at keeping track of firmware updates. We suggest using the most up-to-date firmware from vendors’ official websites: they frequently patch vulnerabilities and mistakes, which can open the point of entry to hackers willing to compromise your network.
Instructions on how to update software are stored on a separate tab in the router’s web interface. All you need to do is download the firmware’s image, back-up the router configuration (sometimes the older file cannot be used with the new firmware, and in that case you might need to run the process from the beginning), run the update and restore the configuration after restarting your system.
Updating #firmware is the easiest and the most necessary step
Tweet
You might use alternative firmware that is developed by enthusiast communities (for instance, OpenWRT), but be cautious: there is no guarantee that the router will run as it is supposed to after the update is completed. Also, even third-party software should be downloaded only from the official websites of well-known projects, do not put your trust in suspicious resources.
Step 7. Not just the router
Absolutely ‘ultimate’ protection does not exist, as the years have proved. A sensible approach to router settings, using strong passwords and encryption and timely updates to firmware will significantly contribute to a higher level of safety for your wireless network, but it does not 100% guarantee your network is safe from hacking.
7 tips for securing your connected home. http://t.co/YMdv5vGrLj by @JacobyDavid via @Securelist #IoT
— Kaspersky Lab (@kaspersky) November 26, 2014
The protection should employ a complex approach, so we recommend using the latest firewalls and antivirus software, with the latest malware databases. Take Kaspersky Internet Security 2015 for example—it allows you to check the security of your wireless network and offers suggestions about applying the correct settings.
 tips
tips