Quite often on various tech sites I read comments asking about the difference between viruses and Trojans and how they are properly analyzed. Sometimes these comments have a lot of merit, sometimes they don’t. After one such – rather delightful – discussion I felt the urge to write about a proper malware examination. Should one run the malware on an “alive” device? Should one sandbox it in a virtual machine? How do you protect yourself and others from harm during such experiments? Also, let’s address a certain Trojan-SMS.AndroidOS.Opfake.a.
Learn how to analyze mobile malware at home #security
Tweet
I will start with a serious question: how do antiviruses fix up an already-infected device? Even a trial version of our product detects and removes a majority of Trojans without any problems.
The Cure
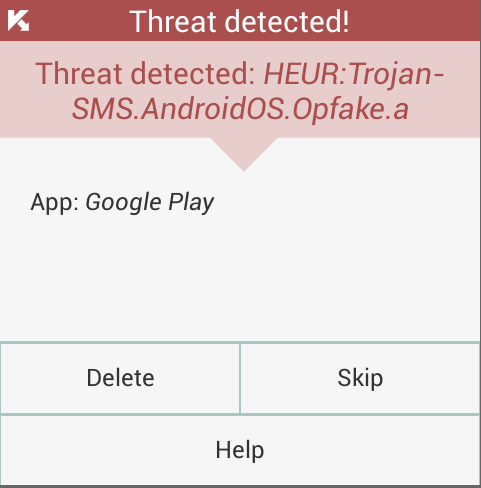
Once a user taps the Delete button, he is automatically sent to the administrative settings menu, where he can revoke the Trojan’s “Device Admin” privileges. Then he is sent to the malware removal menu.
As you can see, the process isn’t completely automated as it is in Windows. Our solution consequentially displays the appropriate menus for the Trojan removal and does all the behind-the-scenes work, but you’ll still have to tap a couple of buttons. Would this task be feasible for an inexperienced user? Well, that’s even more a reason for an inexperienced user to install additional protection means. Had he or she installed the antivirus before, there would be no infection at all.
What is this Trojan and why don’t all vendors detect it at once?
Actually the sms-Trojan family AndroidOS.Opfake is one of the oldest in our collection: the first of them had been detected three years ago, in August 2011. We have intercepted over 8000 variants since then. All of them have the same goal: steal money from the user’s account sending paid SMS texts to a number, and concealing this activities from the user. There are some potential differences. This specific variant Opfake.a first connects to a C&C server and then performs a task it receives. This can be sending spam to the contact list, sending a SMS to premium numbers, or stealing the list of contacts altogether. Other than that the Trojan can intercept incoming SMS texts or even install some other malware.
Interestingly, a modification of the infection displays a picture of a kitten (left). Other ones don’t do this, performing only the hidden malicious operations and showing nothing at all.
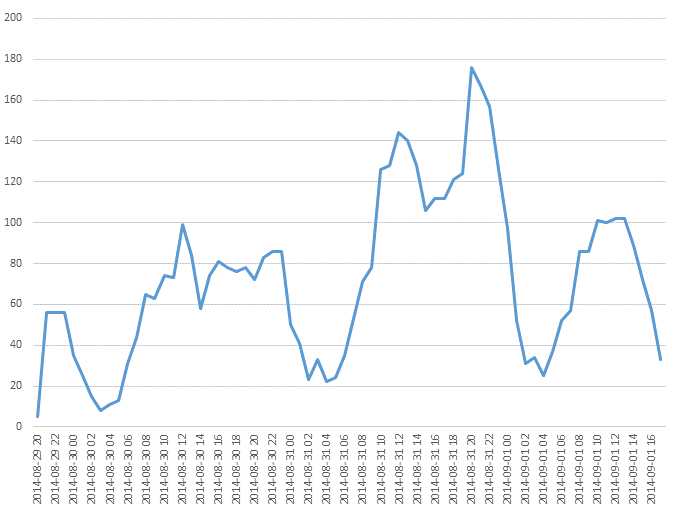
Now, let’s talk about why this Trojan hasn’t been detected by everyone at once. Here’s the graph based on data from our product:
That’s the number of Trojans being detected between August, 29th through September, 1st, in a two-hour interval. As you see, the primary spike was on Aug. 31st, when we detected 1800 attacks overall in Russia, Ukraine, Belarus, Kazakhstan and Uzbekistan. But this modification emerged earlier – on Friday evening of Aug. 29th. Compared to previous versions of the Trojan, the new one was modified in order to circumvent detection methods used in antimalware solutions. But in our case the detection is performed not by signatures, but heuristically – in a nutshell, by the malware behavior. This way we can locate modifications of the same malware, and this method is far more resistant to subtle code modification.
This #opfake variant at least showed that picture of a kitten #security
Tweet
In a situation like this, everything depends on how quickly an antivirus company can react to a new attack. First, the new sample should be caught somehow, then analyzed (by hand or automatically), then “spread the word” across the clients by a product update. An aggravating factor was the time of the initial distribution of the Trojan: apparently the criminals specifically chose the time, keeping in mind our work schedule. Butstillwedelivered :)
Examination
OK, let’s go back to where we have started. We analyze malware by all means possible, and choose the appropriate one (code analysis, emulation, running on a real device) according to the circumstances – and according to our rich experience. What can we recommend to those who would like to analyze such a Trojan at home? First: don’t try it unless you’re absolutely sure you have to do it. Leave it to professionals. In most cases it’s OK to launch the malware on a “fresh” device with no personal data on it: SIM-card is in, but no funds are on the account.
But first I’d suggest using more secure methods:
- Launch a standard Android emulator. This is the safest way to learn more about the Trojan’s functionality. Some malware, however, detect VMs and refuse to work.
- Run this on a real device, but without any personal data and without a SIM card; disable the Web access too. In the case of this specific Trojan this would not do. There are rare types of mobile threats that refuse to work on a device without a SIM, concealing their real purpose.
- Run this on a real device with a SIM card. The lack of funds on your account won’t be a 100% guarantee, so I’d suggest blocking SMS texts to short numbers with your cellular operator.
As I said before, paid SMS sending isn’t the only function of the Opfake, so I wouldn’t recommend using the third method at home. Youhavebeenwarned!
Prevention
We have said before that mobile cybercrime is quite new, but it evolves rapidly, much faster than PC threats. Over the last 2-3 years Android threats went through the same stages of evolution from simple viruses to malware as complex as PC-targeted programs – where it took two decades, not two years. An “advanced” user can easily protect himself from such a Trojan – just don’t open suspicious messages, don’t tap on dubious links and, certainly, don’t install shady apps.
What should less experienced users who more and more often prefer smartphones to the “usual” mobile phones do? Well, if you at least restrict installation of apps from “non-official” sources, Opfake.a already cannot be installed. But this isn’t a 100% security guarantee, which is shown by the dozens of openly malicious apps discovered in Google Play. So it’s necessary to have security software on your mobile devices.
 mobile malware
mobile malware

 Tips
Tips