The idea of renting out malware is not new. Successful malware writers soon hit on the idea that offering their creations to ‘people-with-a-purpose’ could be much more profitable than scouring the Internet themselves in the hope of a big catch. Yet offering a service proved even more profitable. It delivers convenience and simplicity to a much broader clientele, who might otherwise be incapable of using malware themselves (and lack the funds to hire mercenaries ready to do their bidding). Such a wide customer base could be expected to ensure a strong and steady income stream.
The creator of the Adwind Remote Administration Tool felt he could have it all, and more, if he could broaden, not just the customer base, but also the range of affected platforms. So how did that work in practice? Let’s see.
The wind that smells like #RAT: The story of #Adwind #MaaS
Tweet
A RAT with many names and faces
At the end of 2015, an attack on a particular bank in Singapore was attempted. When the attack was discovered, a peculiar specimen of malware came under the microscope of the Kaspersky Lab Global Research and Analysis Team. It was written entirely in Java, and so could be launched under Windows, MacOS, Linux and Android alike. It also possessed surprisingly rich functionality – and considerable resilience to existing security solutions’ detection methods. Such a unique combination of features captured the full attention of Kaspersky Lab’s experts – which in turn led to some interesting results. The malware turned out to be one with many names – including Adwind RAT, Frutas, AlienSpy, Unrecom, Sockrat, JSocket etc – and a short but spectacular history.
It was conceived between 2011 and 2012 by a member of a certain Spanish-speaking hacking forum. The first public release of the Frutas (as it was called back then) malware was in January 2012. The author worked away steadily, and soon its resistance to detection and broad functionality earned the malware wide popularity in the cybercriminal world. Since then, it has changed hands and names several times, gaining in popularity and being continuously improved. Little more than a year after its debut, a subscription model was offered, turning Adwind into a full-scale example of easy-to-use MaaS (Malware-as-a-Service). At the same time, the malware began appearing in targeted attacks across the globe.
The most recent incarnation of this peculiar malware goes under the name of JSocket. It is hard to credit, but its proprietors openly advertise it, as though offering something quite legitimate; and their shadowy hosting provider has so far avoided being located.
Hard to believe these slick, user-friendly webpages are offering highly criminal services
Would-be customers register with a valid email address, choose a subscription plan – and are even ‘upsold’ a wide choice of optional additional modules.
A purposeful and talented RAT
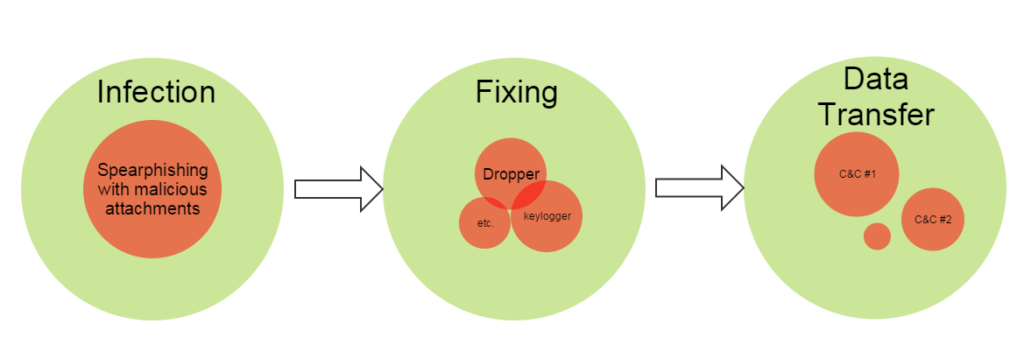
A phishing email with an attachment is the most common starting point for an Adwind-based targeted attack – that or just ‘sand washing’ in search of something useful. The attachment usually looks like a .JAR file, obfuscated and packed several times to complicate detection by static mechanisms. Sometimes it is embedded within an .HTA or even a .DOC/.RTF file. To further confuse existing Windows security systems, the authors purposely use case-sensitive filenames and some other artifacts of *NIX-based development.
Once the attachment is clicked on, the main backdoor is executed. Aside from being able to download and run additional tools, it possesses very broad functionality in itself. For example, it enables the operator to obtain extensive system information, steal passwords, clipboard contents and cryptocurrency keys, record video and audio, grab the keyboard input or set up a proxy server. The attacker can even start a chat with the victim – though it’s difficult to imagine quite how this would go.
The number of known C&Cs is quite extensive and encompasses many geographic regions. There is proof that some Adwind-based targeted attacks directed at Asian-Pacific companies, with major focus on financial institutions, can be linked to the criminal activities of Nigerian immigrants in Malaysia
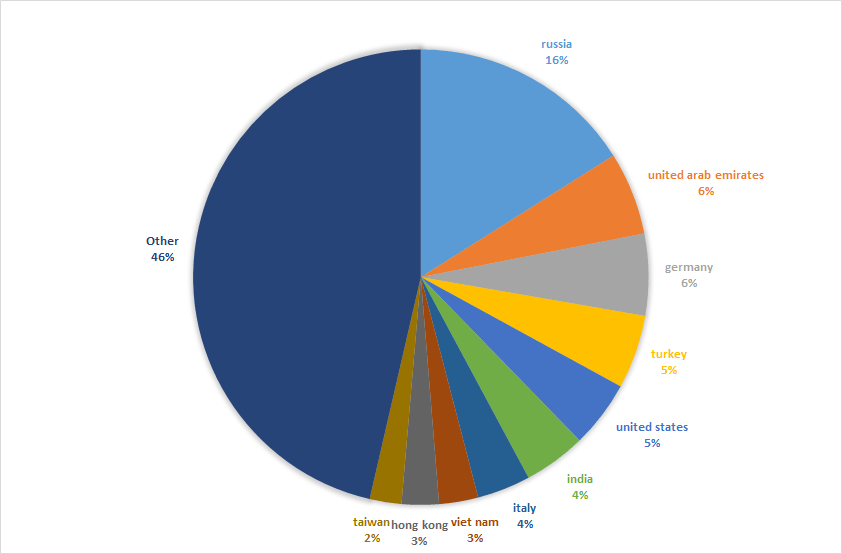
Meanwhile the most attacked regions, regardless of motive, are now Russia, the UAE, Germany, Turkey and the US.
How to trap the RAT
Due to the specifics of pure-JAVA malware, as well as massive packing and obfuscation, many anti-malware engines have problems with Adwind detection. But with extensive Security Intelligence at their disposal, combined with leading-edge detection algorithms powered by continuously running in-Lab Machine Learning processes, Kaspersky Lab’s products are able to detect Adwind samples. Given that (spear)phishing is the main attack vector, setting up a reliable mail security system is extremely important. Kaspersky Security for Mail Servers (which includes a version for Linux) comprises multiple mechanisms to detect and block these dangerous emails. Together with both signature and non-signature malware detection, the solution includes Anti-Phishing supported both by heuristics and by a cloud-assisted reputation system. These technologies allow the detection not just of mail attachments, but also of emails themselves (especially important given that Adwind operators are often careless about their phishing , and casually re-use them ).
A JAVA machine can be a very vulnerable system component nowadays, and, especially in businesses like the banking, workstations performing only a limited number of tasks should ideally be stripped of it completely if mandatory software does not require it. If there is need for it, we recommend restricting some of the double-edged functionality, which could cause considerable harm if abused.
Kaspersky Endpoint Protection for Business comprises a Host-Based Intrusion Prevention System (HIPS, also called Application Privilege Control) providing the administrator with four restriction categories depending on trust level; these groups are also shared with an Application Firewall. To reduce risk, the JAVA interpreter can be put into the Highly Restricted group, severely limiting its (potentially dangerous) capabilities.[1] And if you need to disable JAVA selectively with considerable ease, you can do it by setting up a custom software category and restrict its use on selected endpoints.
Adwind MaaS: time to use a RAT-catcher #protectmybiz
Tweet
It also worth noting that Adwind’s mass phishing emails are often rather unsophisticated, relying on employees’ carelessness and inattentiveness; how many employees would normally receive .JAR files anyway? Such phishing mails being acted on may suggest a lack of understanding of basic cybersecurity principles. This can readily be improved with the help of Cybersecurity Awareness Training available from Kaspersky Lab.
All in all, using multi-layered security is crucial today – as many reports including the widely known ASD Mitigation Strategies keep emphasizing. And it is obviously simpler and more convenient when the majority of these layers are provided by a single vendor and managed through one unified administration console.
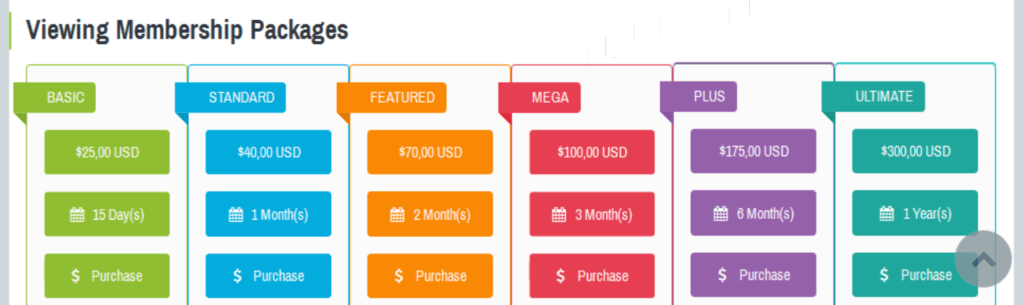
Don’t underestimate the risk: any schoolboy today with a bad attitude and $25 in his pocket could potentially arm himself with an extremely powerful and dangerous toolset offered by Adwind, and do a great deal of harm – even to an Enterprise of considerable size. Highly motivated cybercriminals can do much, much more. Clearly, it is time to arm yourself with a proper RAT-catcher – from the leader in the IT Security Industry.
Kaspersky Lab’s products detect different variations of Adwind with the following verdict:
HEUR:Backdoor.Java.Generic
To know more about Adwind, read this blogpost on Securelist!
[1] The administrator should test the policy carefully before implementation, to ensure any necessary JAVA-based apps functionality is retained.
 Adwind
Adwind

 Tips
Tips