Twitter has recently caught up with competitors like Facebook and Google by improving user protection with two-factor authentication. This will help us all forget about those much talked about account takeovers of the Associated Press and Fox news, which briefly even affected the Dow Jones. The hacking of a personal account is typically not that significant, but is still very unpleasant for the account owner. That’s why we’re using this occasion to remind you of Twitter’s safety rules.
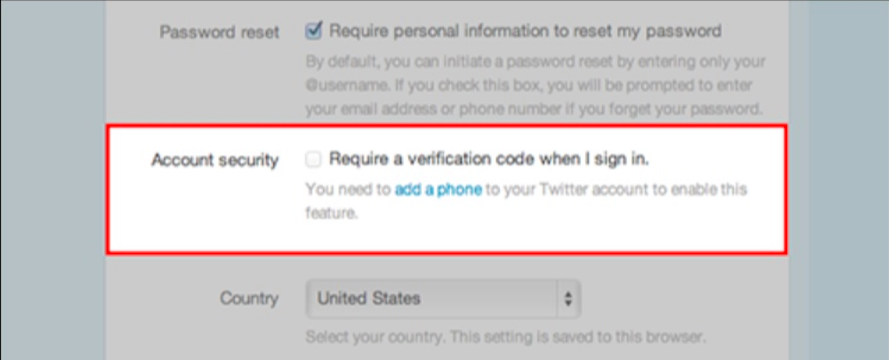
Maximum security. Always select the protection options that provide the maximum level available. For Twitter, it now means switching on two-factor authentication. When you log into Twitter.com you’ll provide not only your username and password, but also a six-digit protection code, sent to your cell phone via text message. Thanks to this measure, it won’t be possible to take over your account even after a password theft. To switch on two-step authentication, you have to log into Twitter, open your account settings and select the option “require a verification code when I sign in.” Next, you’ll need to provide your mobile phone number and follow the onscreen instructions to verify it. Please note, that Twitter is gradually rolling out this function, so it might not be available for your account yet. In this case, check back in a week or two – it should be available after that time.
This authentication method has one significant disadvantage – it makes logging in more complicated when you sign in from a location with bad or absent mobile network coverage. Google solves this issue by remembering your devices and skipping secondary confirmation for up to one month, if you keep logging in from a trusted device. Twitter does eventually plan to ask for the confirmation code each time you log in. In many cases, increased security is worth this inconvenience. However, there may be complications for corporate account owners like the aforementioned Associated Press or Kaspersky Lab. Typically there are several people using one account, but Twitter allows only one phone number for verification. As we were considering our options to setup a workflow with this limitation, someone stole one of our passwords via public Wi-Fi. The attacker briefly took over our German-language Twitter account and sent some spam links to our followers. Of course we regained account control in just a couple of hours and deleted all spammy messages, but we now won’t be waiting before switching on two-factor authentication.
Use strong password. Two-factor authentication doesn’t replace a reliable, hard-to-break password. It has to be long, non-obvious and impossible to guess – it will save you from a brute-force attack targeted at a web service password database. Twitter was even hacked, so this menace is not phantom.
Watch Out for Phishing Pages. You should constantly be on the lookout for phishing scams that ask you for your password or any other sensitive information. If you get an email prompting you to reset your password, but you didn’t request that email, don’t click through. And be careful about clicking through on links from URL shorteners like bit.ly, which have become the unwitting conduits for scammers who want to mask the final destination of that click.
Don’t Use Public Computers or Public Wi-Fi. If it’s not your personal computer, don’t use it to access personal accounts. You have no idea what kind of malware or malicious scripts are running on hotel or airport business center computers or even your friend’s laptop. Public Wi-Fi connections are typically unencrypted, making it easy for any attacker to eavesdrop on you and steal your passwords. If you can’t avoid using an open Wi-Fi network, protect yourself by using a VPN connection.
A note to advanced users
To avoid SMS delivery issues, it’s possible to use third party applications for Twitter access. Previously authorized apps will work as usual even after you switch on two-factor authentication. You can also authorize new apps by logging into Twitter and managing the app’s passwords via settings. However, it’s important to understand, that this shifts the security from Twitter into a specific application and it becomes the developer’s responsibility to protect the app’s users from password and data theft.
 data breach
data breach


 Tips
Tips