UPDATE: Story updated to include expert quotes.
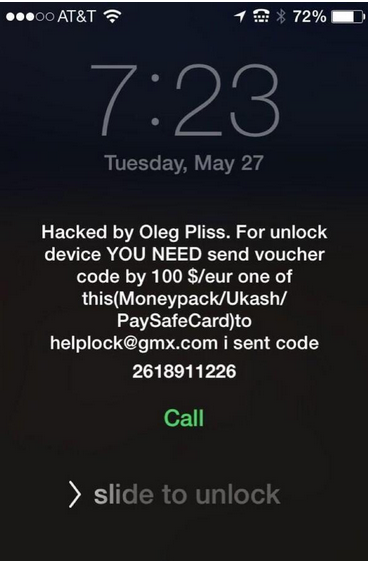
A new piece of ransomware is targeting Apple users, mostly in Australia. Infected users are reportedly seeing a warning message in place of their homescreens offering to unlock affected devices if the user pays a fee between $50 and $100.
According to reports, users first became aware of these infections early yesterday after their iOS and OSX devices’ “Find My iPhone” sound alert began going off. Upon looking at their phone screens, users were presented with a message saying: “Hacked by Oleg Pliss. For unlock YOU NEED send voucher code by 100 $/eur one of this (Moneypack/Ukash/PaySafeCard) to helplock@gmx.com I sent code 2618911226.”
It’s not clear how hackers have managed to compromise affected devices, but the general consensus is that the attackers are leveraging access to users iCloud accounts in order to exploit the phones themselves.
Kaspersky Lab Expert Christian Funk backed up this claim, saying that criminals have been deploying phishing attacks to compromise Apple IDs for a couple years now. Furthermore, Funk pointed us in the direction of a Securelist research article from last summer in which another Kaspersky Lab researcher explained that attackers could launch ransomware campaigns against iOS and Mac devices by accessing iCloud accounts.
It’s also not clear who Oleg Pliss is or if that is even a real person.
Ransomware refers to a class of malware that locks down an infected machine and demands some sort of payment to unlock it. In some cases, the malware merely renders a computer unusable or places some sort of blocker in the way of the user and his or her applications. In others – like the case of CryptoLocker – the ransomware encrypts important files on the infected machine and demands payment for the private key that would decrypt those files.
Paying these ransoms is generally viewed as a bad idea, because you never actually know if anything will get decrypted. This is one of the reasons we always recommend creating regular back-ups of your data. If you have a recent copy of all your data on an external hard drive or some cloud service, then you can just roll your computer back or reinstall the operating system.
A new piece of #ransomware #malware is targeting #Apple users.
Tweet
According to the Sydney Morning Herald, iPhone users in Queensland, NSW, Western Australia, South Australia and Victoria have been targeted by the scheme while several other reports claim users in New Zealand have also been hit. Thus far, users in the U.S. and Europe seem unaffected at the moment, though we wouldn’t be surprised if the problem spread to other continents.
As noted by Chris Brook at Threatpost.com, recent attacks against Adobe and eBay and others have spilled encrypted user passwords. If these passwords were in some way decrypted – and users had shared passwords between services – then the passwords could be easily used in brute force attacks to access online accounts like iCloud. To be clear, affected users would have had to use the same passwords. It’s not clear if there is a connection between these hacks, but in the past, password-spilling data breaches – both known and unknown – have led to online account breaches elsewhere.
If the attack were relying on iCloud account access, that service’s two-factor authentication feature would provide a pretty solid defense. In fact, now might be a good time to turn on two-factor authentication for your iCloud account. Below you’ll find a short screencast that shows you exactly how you can get that process started (we stop just before actually turning on two factor in the video, but I am sure you can figure the rest out).
 Apple
Apple

 Tips
Tips