March brought with it a host of new security stories, and with those stories came our continued promise to keep you informed while providing protection against cybercriminals. From our interactive map of online threats to tips on using our newest safe broswer app, we did our part to keep you in the know. So if you missed any of our posts be sure to catch up now with our monthly roundup of our top March highlights.
Kaspersky Safe Browser for Windows Protects Microsoft-based Smartphones
As new devices and new operating systems come to the market, the list of threats against them continues to grow. That’s why Kaspersky Lab is now offering a safeguard for smartphones that run on Microsoft’s mobile OS system. The Kaspersky Safe Browser for Windows Phone app is designed to protect users from the latest mobile threats, specifically against phishing scams (especially those that revolve around the use of fake sites), while simultaneously offering a set of parental safeguards to restrict the mobile-based Internet activities of children. It evolves as quickly as cybercriminals, because it is constantly updated with solutions to the newest threats through the cloud-based Kaspersky Security Network. “Smartphones are becoming an essential part of modern life and the web browser is one of the most popular features,” said Victor Yablokov, the head of mobile product line at Kaspersky Lab. “However, even the most tech-savvy web user may sometimes struggle to distinguish fake sites from the real thing. Now, Kaspersky Safe Browser for Windows Phone is here to help, providing automatic protection against fraudulent and inappropriate sites.”
Linux Vulnerable to Apple Cert Bug (Sort of)
In the middle of February Apple quietly issued a fix for a critical certificate validation bug in iOS that had the ability to give attackers the capability to spy on supposedly secure communications. The bug not only affected Apple’s mobile iOS operating system, but its traditional OSX operating system as well. Heads really turned when it became apparent that an eerily similar bug affected GnuTLS, a free and open-source piece of software used to implement encryption in various Linux distributions and other platforms. People cried sabotage as experts began noticing that the known coding errors would have been very difficult to miss in the coding review process. Bruce Schneier, one of the world’s premiere cryptography and security experts asked, “Was this done on purpose? I have no idea. But if I wanted to do something like this on purpose, this is exactly how I would do it.”
There has recently been a large peak of interest in Tor, but do you know what it is?
Tor is basically unrestricted, free software operating on the Internet that allows its users to remain anonymous while they are active online. Network traffic is completely anonymous with Tor: it is impossible to identify the user’s IP, making it impossible to determine who the user is in real life. Therefore, no action, like the publication of posts in Tor, can be linked to a particular individual. How is total anonymity possible? All network traffic (i.e. any information) is encrypted repeatedly as it passes through several network nodes, or routers, on its way to Tor. No network node knows either the source of the traffic or the destination or its content. This ensures a high level of anonymity, making it impossible to determine who is behind the network activity, i.e. a real person. Aside from normal users, this technology also attracts the attention of cybercriminals who have started using Tor as an underground market, popularizing the now infamous Bitcoin while also using it to host malicious infrastructure like ChewBacca and the first Tor Trojan for Android.
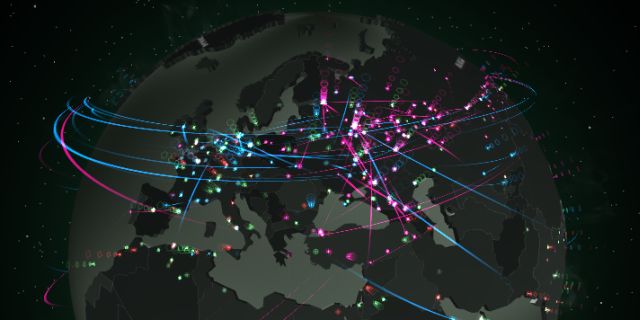
Look at Cyberwar With Your Own Eyes: An Interactive Map of Online Threats
In today’s world, it takes minutes for new malware applications or spam to be distributed, but now you can see the scale and magnitude of the problem with your own eyes thanks to our map depicting malware epidemics in real time. Which country gets more spam in the morning: Germany or USA? Who more readily clicks on malicious links: Russians or Japanese? Which country leads in terms of malware infection rates? Our map lays all this information out for you. Interactive in nature, it allows you to move around the globe while showing you the different threats that currently exist and what the most infected countries are. Most importantly though, it gives you the opportuity to check your PC for viruses free of charge in to prevent further exposure to malware by clicking on the ‘Check my PC’ button offered.
How to Use Kaspersky Protection With The New Versions of Google Chrome
Google, which recently announced that the Chrome browser will now be working with extensions only from the official Chrome Web Store, in the hopes of better protecting users against vulnerable, malicious, and annoying extensions, plug-ins, and other additions, which can override user’s settings and/or alter the user experience in undesired ways. However, as the developer of security products, we faced a problem here: how do we protect our customers against phishing, malicious web sites, key loggers and other threats when, starting from version 33, the browser won’t work with our old extensions? We’re now offering a new Google Chrome plug-in — Kaspersky Protection. This extension is bundled with the recently released patch F and includes three parts: Virtual keyboard, Safe Money and Block dangerous websites module, making your Internet browsing even more safe and secure.
Hacking The Airport Security Scanner
A presentation on the subject of Airport cybersecurity was recently given at the SAS 2014 Conference by Qualys researchers Billy Rios and Terry McCorkle, who spent time exploring a very important system of the airport protection perimeter – an X-Ray introscope. This device is controlled by a special key panel, and is essentially a highly specialized scanner connected to an ordinary PC running software on top of a typical Windows installation. Upon a deeper dive of the software, Rios and McCorkle discovered the computer was running Windows 98, which is 15 years old and no longer supported by Microsoft, causing worry over how many exploitable and unpatched vulnerabilities still exist in it. They also found out the system focused heavily on physical security while neglecting computer security. Although this raised some alarm, airport security zone computers are isolated from the Internet, making it very difficult to hack them, and this test was conducted on just one, older system. Airports do have other security measures in place so there is no need to truly panic, but this has taught us that traditional security measures like administrative access control and “airgapping” (network isolation) are no replace for a dedicated layer of cyber-security.
 Cybersecurity
Cybersecurity
 Tips
Tips