Computers, initially created for military cipher breaking, give everyone an almost perfect way to keep our secrets totally private – through encryption. For a long time strong encryption was only available to governments, but now it can be used by any user. More importantly, even if you never considered it before, you always have secrets worth encrypting.
Something to hide
When discussions regarding encryption and protection start people often say, “I have no secrets, nothing to hide.” However, typically they mean, “I believe no one will bother to dig into my smartphone or laptop to find something valuable.”
But it turns out that such hopes are not likely true. A document saved on a home PC desktop or a cell phone left in a living room could quickly become an object of examination for those around you. Are you ready to show all your letters, photos and documents to your wife, brother or kids? Maybe there is nothing bad saved, but you still may not be willing to share. Are you ready to tell your credit card number and PIN code to your teenage children? Give away your Gmail or Facebook password to your sister? Show all your family photos to your friends, who may be visiting your house and borrowing your PC for 15 minutes?
Do you really want to explain to your wife that Natasha is a colleague from another department of the company you work for and the “meeting tomorrow” you’re discussing is really a business meeting with ten participants?
Of course, a story could become even more embarrassing if a malicious application manages to infect your computer. A recent trend in the cybercriminal world is a malware that can steal all potentially valuable information from your computer: documents, photos, passwords, saved in a web browser – everything.
Stolen images often contain document scans, i.e. a photo of your drivers license and other important papers potentially useful in fraud and identity theft. There have even been cases when stolen images with saucy photos were used for blackmail.
Another new disaster for users is a forgotten smartphone. As this type of phone is typically full of valuable private information, some “advanced” thieves not only resell these stolen devices, but scan their memory in search of useful data like passwords and mobile banking codes/apps.
One answer for all troubles
There are a lot of threats to your information, but it’s possible to develop protections for each like by isolating your home PC from strangers and minors and using a PIN on your phone lock screen, etc.
There is also a more versatile way – to make information readable only by a legitimate owner. All those awkward moments and mishaps might be avoided if private information is stored in an encrypted form.
You encounter encryption even when you don’t think about it when you’re checking Gmail or banking via HTTPS or calling your friend using a popular GSM cellular network. But we want to concentrate on another important aspect – encrypting the data stored on your computer or smartphone.
What is encryption
Encryption is the process of transforming information in such a way that an unauthorized third party cannot read it; a trusted person can decrypt data and access it in its original form though. There are a lot of popular encryption/decryption methods, but the key to security is not a proprietary algorithm. The most important thing is keeping the encryption key (password) a secret so only trusted parties know it.
It is important to distinguish encoding from encryption. Encoding also transforms information, but it’s typically performed for the convenience of storage or transmission, not keeping secrets. Widely known encoding methods are Morse code and binary encoding for computer storage.
Your digital locker
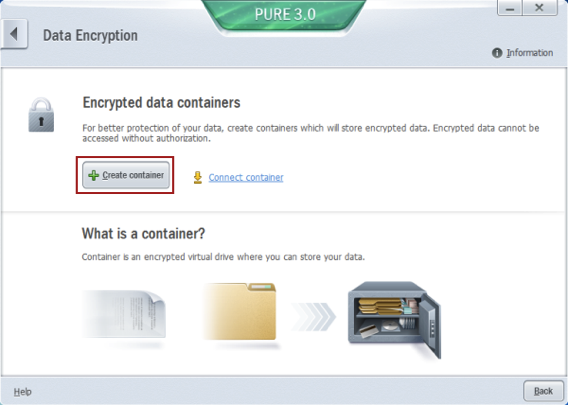
The most convenient solution to keeping files encrypted is the creation of an encrypted vault, also known as a container. When mounted, it’s visible in the system as a separate disk drive. You can save or copy any files on it and use it just like your USB stick. The important difference is that a physical container is a big file on your hard drive, and you access it via special software like Kaspersky PURE. Any file you save to this special drive will be encrypted “on the fly” and saved to one big container file.
Any person that has access to your PC can see and even steal (copy) a container file, but it won’t really help the thief to access your information. Only random characters are inside this file and it can take years to find the password able to transform this file full of garbage to a disk with readable files.
Of course, you have to follow some simple rules to make an encrypted container an effective protection:
* Your encryption key (password) is the only protection against others. You have to make it long, complicated and hard to guess. Here are our tips on making good password.
* You have to store all your private information on the encrypted drive.
* Any person that knows the password can read all files stored. If you have different types of information and want to make it accessible to different users, you can create multiple containers with different passwords.
* This is very important! Don’t keep your encrypted drive mounted. If you do, anyone can steal your files as if they are from an ordinary disk. Mount your encrypted drive only when working with important data and dismount immediately after finishing your job.
* If a container file is somehow damaged, all files stored will be lost. That’s why it’s important to backup container files often.
* Use total protection of your computer – we suggest Kaspersky PURE – to protect your encryption password from trojans and keyloggers. An active keylogger diminishes your encryption efforts.
Smartphone safety
In trying to protect users data from smartphone theft, mobile OS vendors have developed encryption functions. Important information is kept in an encrypted form and is decrypted each time a user inputs his PIN to unlock his device. Apple doesn’t allow users to manipulate encryption settings, but a lot of information is encrypted when you activate the passcode protection. There is a full content encryption option in the Android security settings, and it makes all user data inaccessible without a password. To ensure maximum protection we recommend using recent versions of mobile OS – iOS 6.1+ and Android 4.1+.
Cloud protection
There is one type of information that desperately needs to be encrypted: your passwords. You have to use a unique and strong password for each site and service, but it’s complicated to memorize all of them. The solution is using a special password storage application, called digital wallets, which constantly keep your password database encrypted.
Strong encryption allows the safe transmission of this database to the Internet and syncs it between different computers and mobile devices. Cloud services of this kind allow you to keep all of your passwords handy without sacrificing security.
 data security
data security



 Tips
Tips